Error message
Warning: Undefined variable $state_label in enisaweb_preprocess_node() (line 443 of /var/www/html/lib/themes/enisaweb/enisaweb.theme).
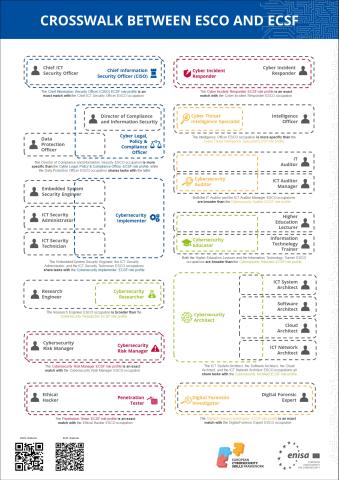
The ECSF and the ESCO classification share a common objective: to analyse
the labour market in terms of professional roles and required skills, albeit from different perspectives. ESCO aims to classify the entire EU labour market across various sectors, while the ECSF provides a focused analysis of role profiles specific to the cybersecurity sector.
During the update process leading to the release of ESCO version 1.2, ENISA collaborated closely with the ESCO team. Leveraging the ECSF, several enhancements were made to the ESCO classification to more accurately represent the occupations and skills required in cybersecurity.
As a result of this collaboration, ESCO v1.2 now includes 5 occupations that are directly aligned with 5 ECSF cybersecurity role profiles. Additionally, 7
ECSF profiles are associated with multiple ESCO occupations, linked by
shared tasks, skills, and scopes, each with varying degrees of correspondence.
The document titled "Crosswalk between ESCO and ESCF" details this collaboration and its outcomes.
The table below outlines the relationship between ESCO occupations (including their respective ESCO codes) and ESCF role profiles.
| ESCO code | ESCO Occupation v 1.2 | ESCO Occupation Description | Relationship | ECSF role profile | ECSF summary statement |
| 2529.1 | Chief ICT security officer | Chief ICT security officers protect company and employee information against unauthorized access. They also define the Information System security policy, manage security deployment across all Information Systems and ensure the provision of information availability. | The ESCO occupation is an exact match with the ECSF role profile | Chief Information Security Officer (CISO) | Manages an organisation’s cybersecurity strategy and its implementation to ensure that digital systems, services and assets are adequately secure and protected. |
| 2529.7 | Cyber incident responder | Cyber incident responders monitor and assess cybersecurity state systems, analysing, evaluating, and mitigating the impact of cybersecurity incidents. Moreover, they identify malicious actors and cyber incident root causes. According to the organisation’s Incident Response Plan, they restore systems and process functionalities to an operational state, collecting evidence and documenting actions taken. | The ESCO occupation is an exact match with the ECSF role profile | Cyber incident responder | Monitor the organisation’s cybersecurity state, handle incidents during cyber-attacks and assure the continued operations of ICT systems. |
| 1213.9 | Director of compliance and information security | Directors of compliance and information security follow the regulatory compliance and oversee information security to ensure the security of all information technology associated. | The ESCO occupation is more specific than the ECSF role profile | Cyber Legal, Policy & Compliance Officer | Manages compliance with cybersecurity-related standards, legal and regulatory frameworks based on the organisation’s strategy and legal requirements. |
| 2619.4 | Data protection officer | Data protection officers ensure that the processing of personal data in an organisation is compliant with data protection standards and with the obligations set out in the applicable legislation such as GDPR. They elaborate and implement the organisation policy related to data protection, are responsible for data protection impact assessments and handle complaints and requests from third parties and regulatory agencies. | The ESCO occupation shares tasks with the ECSF role profile | Cyber Legal, Policy & Compliance Officer | Manages compliance with cybersecurity-related standards, legal and regulatory frameworks based on the organisation’s strategy and legal requirements. |
| 2422.8 | Intelligence officer | Intelligence officers develop and execute plans to gather information and intelligence. | The ESCO occupation is broader than the ECSF role profile | Cyber Threat Intelligence Specialist | Collect, process, analyse data and information to produce actionable intelligence reports and disseminate them to target stakeholders. |
| 2511.14 | ICT system architect | ICT system architects design architecture, components, modules, interfaces, and data for a multi-component system to meet specified requirements. | The ESCO occupation shares tasks with the ECSF role profile | Cybersecurity Architect | Plans and designs security-by-design solutions (infrastructures, systems, assets, software, hardware and services) and cybersecurity controls. |
| 2512.3 | software architect | Software architects create the technical design and the functional model of a software system, based on functional specifications. | The ESCO occupation shares tasks with the ECSF role profile | Cybersecurity Architect | Plans and designs security-by-design solutions (infrastructures, systems, assets, software, hardware and services) and cybersecurity controls. |
| 2512.6 | cloud architect | Cloud architects are responsible for converting the technical features of a project into the architecture to lead to the final product. | The ESCO occupation shares tasks with the ECSF role profile | Cybersecurity Architect | Plans and designs security-by-design solutions (infrastructures, systems, assets, software, hardware and services) and cybersecurity controls. |
| 2523.2 | ICT network architect | ICT network architects design the topology and connectivity of ICT networks such as hardware, infrastructure, communication and hardware components. | The ESCO occupation shares tasks with the ECSF role profile | Cybersecurity Architect | Plans and designs security-by-design solutions (infrastructures, systems, assets, software, hardware and services) and cybersecurity controls. |
| 2511.18 | IT auditor | IT auditors perform audits of information systems, platforms, and operating procedures in accordance with established corporate standards for efficiency, accuracy and security. They evaluate ICT infrastructure in terms of risk to the organisation and establish controls to mitigate loss. They determine and recommend improvements in the current risk management controls and in the implementation of system changes or upgrades. | The ESCO occupation is broader than the ECSF role profile | Cybersecurity Auditor | Perform cybersecurity audits on the organisation’s ecosystem. Ensuring compliance with statutory, regulatory, policy information, security requirements, industry standards and best practices. |
| 2519.2 | ICT auditor manager | ICT auditor managers monitor ICT auditors responsible for auditing information systems, platforms, and operating procedures in accordance with established corporate standards for efficiency, accuracy and security. They evaluate ICT infrastructure in terms of risk to the organisation and establish controls to mitigate loss. They determine and recommend improvements in the current risk management controls and in the implementation of system changes or upgrades | The ESCO occupation is broader than the ECSF role profile | Cybersecurity Auditor | Perform cybersecurity audits on the organisation’s ecosystem. Ensuring compliance with statutory, regulatory, policy information, security requirements, industry standards and best practices. |
| 2310.1 | Higher education lecturer | Higher education lecturers instruct students who have obtained an upper secondary education diploma in their own specialised field of study, which is predominantly academic in nature. | The ESCO occupation is broader than the ECSF role profile | Cybersecurity Educator | Improves cybersecurity knowledge, skills and competencies of humans. |
| 2356 | Information technology trainer | Information technology trainers develop, schedule and conduct training programmes and courses for computer and other information technology users outside the mainstream primary, secondary and higher education systems | The ESCO occupation is broader than the ECSF role profile | Cybersecurity Educator | Improves cybersecurity knowledge, skills and competencies of humans. |
| 2529.3 | Embedded system security engineer | Embedded systems security engineers advise and implement solutions to control access to data and programs in embedded and connected systems. They help ensuring the safe operation of products with embedded systems and connected devices by being responsible for the protection and security of the related systems and design, plan and execute security measures accordingly. Embedded systems security engineers help to keep attackers at bay by implementing safeguards that prevent intrusions and breaches. | The ESCO occupation shares tasks with the ECSF role profile | Cybersecurity Implementer | Develop, deploy and operate cybersecurity solutions (systems, assets, software, controls and services) on infrastructures and products. |
| 2529.6 | ICT security administrator | ICT security administrators plan and carry out security measures to protect information and data from unauthorised access, deliberate attack, theft and corruption. | The ESCO occupation shares tasks with the ECSF role profile | Cybersecurity Implementer | Develop, deploy and operate cybersecurity solutions (systems, assets, software, controls and services) on infrastructures and products. |
| 3512.3 | ICT security technician | ICT security technicians propose and implement necessary security updates and measures whenever is required. | The ESCO occupation shares tasks with the ECSF role profile | Cybersecurity Implementer | Develop, deploy and operate cybersecurity solutions (systems, assets, software, controls and services) on infrastructures and products. |
| 2149.2.8 | Research engineer | Research engineers combine research skills and knowledge of engineering principles to assist in the development or design of new products and technology. They also improve existing technical processes, machines and systems and create new, innovative technologies. The duties of research engineers depend on the branch of engineering and the industry in which they work. Research engineers generally work in an office or laboratory, analysing processes and conducting experiments. | The ESCO occupation is broader than the ECSF role profile | Cybersecurity Researcher | Research the cybersecurity domain and incorporate results in cybersecurity solutions. |
| 2529.8 | cybersecurity risk manager | Cybersecurity risk managers identify, analyse, assess, estimate and mitigate cybersecurity-related risks of ICT infrastructures such as systems or services. They manage these aspects by planning risk analysis, applying, reporting, assessing, communicating, and treating them. They establish a risk management strategy for the organisation and ensure that risks remain at an acceptable level for the organisation by selecting mitigation actions and controls. | The ESCO occupation is an exact match with the ECSF role profile | Cybersecurity Risk Manager | Manage the organisation's cybersecurity-related risks aligned to the organisation’s strategy. Develop, maintain and communicate the risk management processes and reports. |
| 2529.2 | Digital forensic expert | Digital forensics experts retrieve and analyse information from computers and other types of data storage devices. They examine digital media that may have been hidden, encrypted or damaged, in a forensic manner with the aim to identify, preserve, recover, analyse and present facts and opinions about the digital information. | The ESCO occupation is an exact match with the ECSF role profile | Digital Forensics Investigator | Ensure the cybercriminal investigation reveals all digital evidence to prove the malicious activity. |
| 2529.4 | Ethical hacker | Ethical hackers perform security vulnerability assessments and penetration tests in accordance with industry-accepted methods and protocols. They analyse systems for potential vulnerabilities that may result from improper system configuration, hardware or software flaws, or operational weaknesses. | The ESCO occupation is an exact match with the ECSF role profile | Penetration Tester | Assess the effectiveness of security controls, reveal and utilise cybersecurity vulnerabilities, assessing their criticality if exploited by threat actors. |
